The traditional approach to security—treating it as a final checkpoint before deployment—has become a liability in modern software delivery. After two decades of building enterprise systems, I’ve witnessed the painful evolution from “security as an afterthought” to “security as code.” In 2025, DevSecOps isn’t just a best practice; it’s a survival requirement for any organization shipping software at scale.
The Shift Left Revolution
The concept of “shifting left” has transformed from buzzword to operational reality. When I started my career, security reviews happened weeks before release—often discovering critical vulnerabilities that required expensive rework. Today’s DevSecOps pipeline integrates security at every stage, from the first line of code to production monitoring.
The economics are compelling: fixing a security vulnerability in production costs 100x more than catching it during development. More importantly, the velocity of modern CI/CD pipelines—often deploying dozens of times per day—makes traditional security gates impossible to maintain without automation.
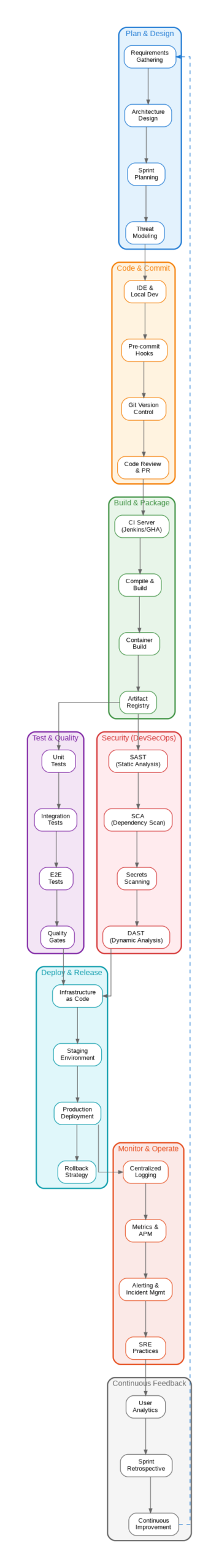
The Eight Pillars of Modern DevSecOps
A mature DevSecOps implementation spans eight interconnected stages, each with its own security considerations and tooling requirements.
1. Plan and Design
Security begins before any code is written. Threat modeling during the design phase identifies potential attack vectors and informs architectural decisions. Tools like Microsoft Threat Modeling Tool or OWASP Threat Dragon help teams systematically analyze risks. The key insight: security requirements should be first-class citizens in your backlog, not afterthoughts added during code review.
2. Code and Commit
The developer’s workstation is the first line of defense. Pre-commit hooks can catch secrets, validate code patterns, and enforce security policies before code ever reaches the repository. IDE plugins from vendors like Snyk, SonarQube, or GitHub Advanced Security provide real-time feedback as developers write code. This immediate feedback loop is crucial—developers learn secure coding patterns through continuous reinforcement rather than delayed security reviews.
3. Build and Package
The CI server becomes a security checkpoint. Static Application Security Testing (SAST) analyzes source code for vulnerabilities without executing it. Software Composition Analysis (SCA) scans dependencies for known CVEs—critical given that 80% of modern applications consist of third-party libraries. Container image scanning ensures base images and layers don’t introduce vulnerabilities into your deployments.
4. Test and Quality
Beyond functional testing, security-focused test suites validate authentication flows, authorization boundaries, and input validation. Dynamic Application Security Testing (DAST) tools like OWASP ZAP or Burp Suite probe running applications for vulnerabilities that only manifest at runtime. Interactive Application Security Testing (IAST) combines both approaches, instrumenting applications during test execution.
5. Security Gates (The DevSecOps Differentiator)
This is where DevSecOps diverges from traditional DevOps. Automated security gates enforce policies without human bottlenecks. Critical vulnerabilities block deployment automatically. Medium-severity issues might require acknowledgment. Low-severity findings get tracked but don’t stop the pipeline. The key is calibration—too strict and you create friction that developers work around; too lenient and you ship vulnerable code.
6. Deploy and Release
Infrastructure as Code (IaC) brings security to deployment configurations. Tools like Terraform, Pulumi, or AWS CloudFormation should be scanned for misconfigurations—open S3 buckets, overly permissive IAM policies, or unencrypted storage. Runtime protection through Web Application Firewalls (WAF), API gateways, and service meshes provides defense in depth.
7. Monitor and Operate
Production security requires continuous vigilance. Security Information and Event Management (SIEM) systems aggregate logs and detect anomalies. Runtime Application Self-Protection (RASP) monitors application behavior and blocks attacks in real-time. Cloud Security Posture Management (CSPM) continuously validates cloud configurations against security benchmarks.
8. Continuous Feedback
The DevSecOps loop closes with feedback mechanisms that improve future iterations. Security metrics—mean time to remediation, vulnerability density, false positive rates—inform process improvements. Post-incident reviews identify systemic weaknesses. Bug bounty programs and penetration testing provide external validation.
Implementation Lessons from the Field
Having implemented DevSecOps transformations across multiple enterprises, I’ve learned several hard lessons. First, tool sprawl is real—the security tooling landscape is fragmented, and integrating multiple point solutions creates maintenance burden. Platform approaches from GitHub, GitLab, or Azure DevOps that provide integrated security features often deliver better outcomes than best-of-breed tool chains.
Second, developer experience matters enormously. Security tools that generate thousands of false positives or require context-switching to separate dashboards get ignored. The most successful implementations embed security findings directly in pull requests and developer workflows.
Third, cultural change is harder than technical change. DevSecOps requires security teams to become enablers rather than gatekeepers. Developers need to own security outcomes, not just throw code over the wall. This shift requires executive sponsorship, training investment, and patience.
The 2025 Landscape
Several trends are reshaping DevSecOps in 2025. AI-powered security tools are reducing false positives and prioritizing vulnerabilities based on exploitability and business context. Supply chain security has become paramount following high-profile attacks—SBOM (Software Bill of Materials) generation and attestation are becoming standard requirements. Zero-trust architectures are extending DevSecOps principles beyond the pipeline into runtime environments.
The regulatory landscape is also evolving. The EU’s Cyber Resilience Act, updated NIST frameworks, and industry-specific requirements like PCI DSS 4.0 are mandating security practices that DevSecOps naturally provides. Organizations that haven’t adopted these practices face not just security risks but compliance penalties.
Getting Started
For organizations beginning their DevSecOps journey, I recommend starting with three high-impact, low-friction changes: enable secret scanning in your repositories (most platforms offer this free), add dependency scanning to your CI pipeline, and implement basic SAST for your primary programming languages. These three controls catch the majority of common vulnerabilities without significant process changes.
From there, expand incrementally—add container scanning, implement security gates, integrate DAST into staging environments. The goal isn’t perfection on day one; it’s continuous improvement toward a security-first culture.
DevSecOps isn’t optional in 2025—it’s the price of admission for shipping software responsibly. The organizations that thrive will be those that treat security not as a tax on velocity but as an enabler of sustainable speed.
Discover more from C4: Container, Code, Cloud & Context
Subscribe to get the latest posts sent to your email.